
Almost 15 years have passed since 9/11 and now the global Homeland Security (HLS), Counter-terrorism & Public Safety markets are going through major shifts. The EC just experienced two horrifying terror acts in Brussels and Paris. Our expert commentator and Managing Editor Intelligence Technology Michael Fayerman tell how “Big Data” Analytical Platforms could assist Law Enforcement and Military structures in preventing terrorist acts and become important part of Defense Companies offerings.
By Michael Fayerman
Managing Editor/ Intelligence Technology Expert,
Defence and Intelligence Norway
At the high level, there two integrated ways of countering this plague of 21 century. First, the most important is to make counter-terror operations a part of the comprehensive government policy. In case of EC it has to change some of their fundamental political policies. Currently, Europe views person actions including drug trade or terrorism is the”fault” of the society that created this problem. That policy of political correctness has to go. Security has to become a key human right that just as important as other rights if not more so.
The EC needs political will to create a top down anti-terror set of policies that involve cooperation of all government agencies such as police, intelligence , military, finance, social, immigration that is supported by new legislative decisions. However the main focus of this paper is to look on a set of new solutions and strategies that were born originally in military tactics and technology that is sporadically are used for counter-intelligence and other type of asymmetrical warfare. But the quick advances in these technologies require an appropriate changes in their adoption by properly choosing these technologies and match them to required methods and functions.
The markets once dominated by the U.S. key Defense Contractors, following the January 2015 ISIS terror attacks in Paris and now Belgian attacks are now moving to the EC, ME and the Asia Pacific markets. The counter-terrorist and security management technologies will experience significant growth due to scope and sophistications of terrorist groups in these areas. Reliance on a handful of major defense contractors alone, cannot meet these requirements that require innovation and agile delivery cycles. This market requires innovation that could be provided by start-ups or vertically dedicated spin-offs that focus on various technical challenges related to monitoring and preventing terrorist actions. Eventually, the “best in class” small player’s solutions will be integrated via partnerships or acquisition by large world players in that market.
Urban living is soon to become the dominant form of human habitation. In 2014, more than half the global population resided in cities. It’s expected that in 2017, this will be true of even less developed countries. As populations relocate to dense urban population centers, the cities themselves are growing, giving rise to mega-cities that are set to dominate the landscape in many countries.
Dense population with transit hubs and other places mass assembly of all types present an attractive target for terrorist imported or homegrown cells and belligerent actors( “lone wolfs) while the depletion of rural populations combined with advances in sensing and weapons systems mean that hiding in remote areas is becoming increasingly unattractive for terrorists. For the militant elements of society, the impenetrable clutter of the modern city is an attractive and alluring prospect. culture, and the “mega-regions” that develop when cities grow and fuse to create population centers stretching over hundreds of kilometers and housing populated by millions of people
One of the challenges today is coping with a “tsunami” of information coming in from an array of information sources that reside in poly-formats on various technology platforms, leading to a very loaded picture that is very hard to make sense of. The practical challenge is to manage the information along with control & command together on the same platform. The greatest challenge is creating an optimal system for the.military, counter terror experts or police.
Traditional warfare is replaced by insurgency and asymmetrical warfare.
Nevertheless, this shouldn’t spell doom to the prospects of safety and security. Advancements in science and IT which in turn create new and maturing intelligence and HLS technologies. These changes create new market niches and fresh business opportunities for innovative ways that could work as preventive measures to fight terror and asymmetrical warfare. The multi-billon fighter jets become less valuable than the software that could help law enforcement and military to accurately predict insurgency activities and predict potential terror attacks. Their objective is to answer with high confidence three basic key questions : WHERE, WHO and WHEN. By knowing this information the counter terror forces could establish first virtual and then physical control of the potential events.
Enormous amounts of data are already available, from a myriad of cameras, monitoring devices, sensors deployed in cities around the globe. What is needed is a fundamental shift in the approach to understanding the environment. Security forces of today must generate a holistic approach that utilizes all this information with the aid of Big Data analytics. These new tools need to replace legacy systems with the new architecture that exponentially increase efficiency as compared to the legacy applications. Although, Michael Dell stated that Big Data will become $1trillion market, these shifts lead to $349 billion 2014 market that will grow to a $546 billion market by 2022. There are another estimated $200 billion dollars of emergency funds allocated annually by the US government to address these challenges. These changes require new approach in product development and system integration methodologies in data management.
One example of these emerging market niches is Terrain Dominance Analysis Platform for Intelligence (TDAPI) – a military tactical/strategic intelligence data collection, integration and analysis model based on military concept called Terrain Dominance coupled with advanced technologies aimed at providing full view of pertinent information within a defined area over time. Both in military a) operations, tactical/military intelligence, wide counter terrorism and b) “safe city” capabilities based on advanced technologies aimed at offering 360 degree integrated intelligence view for a dedicated physical urban or other areas.
 Yet EC counter-terrorist organizations could not prevent or catch the key terrorist players behind the very sophisticated multi-person terrorist attack in Paris took many innocent lives. Same happened in Brussels attack. After month of Europe wide search, ISIS operative and Paris attacker, Salah Abdelslam, found hiding out among his known friends in largely muslim area of Brussels, Belgium. In a sense it was a terrorist cell that spreads all over EC. Why Paris and Belgian counter-terrorist organizations could not prevent and identify the existing network of militants? Also why did it take almost half of the year to catch him? As mentioned earlier a policy aspect is not within the scope of this paper.
Yet EC counter-terrorist organizations could not prevent or catch the key terrorist players behind the very sophisticated multi-person terrorist attack in Paris took many innocent lives. Same happened in Brussels attack. After month of Europe wide search, ISIS operative and Paris attacker, Salah Abdelslam, found hiding out among his known friends in largely muslim area of Brussels, Belgium. In a sense it was a terrorist cell that spreads all over EC. Why Paris and Belgian counter-terrorist organizations could not prevent and identify the existing network of militants? Also why did it take almost half of the year to catch him? As mentioned earlier a policy aspect is not within the scope of this paper.
As one Big Data thought leader from EC stated in his presentations that everyone one claims that they doing Big Data analytics but in reality very few even understand what that really means.Verbatim “its like teenage sex. Everyone talks about it, nobody really knows how to do it, everyone thinks everyone else is doing it,so everyone claims they are doing it.” The main point that we still in a very early stages of adoption, development and implementation of the Big Data products and applications. across all industries Some industries such as marketing and advertising have higher lever of adoption. Others trying to get “final couple of miles” from the legacy Data Management and Analysis systems. The good news that the base technology getting better and easier to implement.
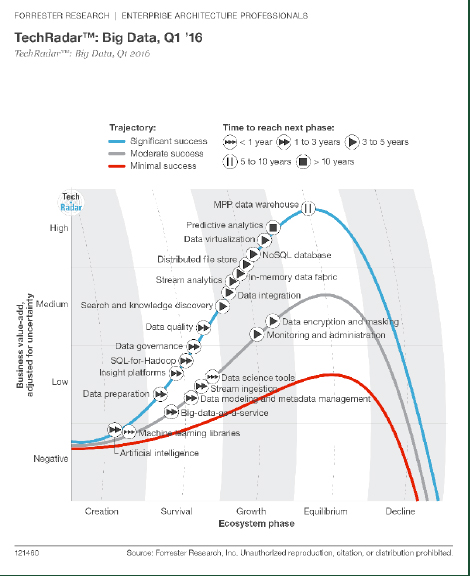
Although Data Warehousing has been around for several decades, new technologies that became available recently will change Big Data Management and Data Analytics are developed and delivered to the consumer. The architecture will target less IT segment but via the following functions such as“ data democratization”, embedded analytics , real time (if needed),machine learning , poly-data streaming will offer more simplified, data modeling and data delta management, data streaming ,data quality and distribution mechanisms. The key objectives in developing effective Big Data Platforms to pick right tools, good engineering that minimize going forward development efforts and create vertically oriented API, Web Services and algorithms libraries that support requirements for specific business or industry. The other efficiency will be accomplished by delivering right knowledge, to the right consumer at the right time. If the capability to make Advanced Analytic Cycle embedded and offer machine driven reengineering, Michael Dell’s prediction on size of the market may become materialized. The production of vertically oriented AI based analytical platforms will make processes smarter and more perspective than ever before. In that case, military platforms will be measured less by “metal” and more on “smart” analytical applications. Forester’s research produced a chart representing the importance and priority of these functions, I
One example of these vertical systems is Terrain Dominance Data Analysis for Intelligence Platform (TDAIP) that could offer real time advanced data driven cognitive based platform that offers to military, intel and law enforcement organizations terrain dominance capabilities by enabling tactical and strategic advantage to pre-empt risks of unexpected violence in a field or the city by providing real time data streams that embed “ ready to consume “ analysis data that offers tactical or strategic advantage by utilizing various inputs such as video, sensors,social networks, GIS and structured and unstructured formats,etc.
The next generation of embedded analytics intelligence platform will leverage self-learning via AI and designed to reduce the complexity of poly-data processing by implementing domain-specialized business services layer and mash-ups of intelligence data sources using an intuitive modeling user interface with user-defined filters, constraints and business rules, widget-based modeling, third-party models integration, hiding the complexity of multiple layers of real-time streaming, data management, machine learning and complex analytics.
- The goal of these platforms is meant to reduce the implementation timeline and minimize the costly efforts associated with the custom software development, “learns” business patterns and becomes faster and “smarter” with every new data source and new scenario that is defined by the user, using a super-posed layered approach. The accuracy and efficiency of the platform grows exponentially with more data and experience.
- Vertically oriented data driven analytical platforms should include only necessary components to integrate with data sources, sophisticated but userfriendly interface to enable appropriate analytical self-service workflow that includes but not limited to deep learning/neural network capability to enable self learning models and to put more power into the hands of the data scientists and SME’ users and minimize development activities.
- In addition, imagine that you employ advanced analytics to codify the approach of the best, most experienced intelligence analysts. You build an analytic model that captures their decision logic. Then it becomes part of your algorithm libraries. Include open API integration libraries, or using web services and in some cases build connectors with ability to integrate with input data and front end analytical or visual tools in order to preserve customer existing investment into BI and ability to scale to support up to 1000 concurrent users.
- Also, the platform should enable “Machine-process improvement” not only by creating new workflows, but a wholly new model for thinking about work and processes. It has the potential to augment our thinking beyond cause and effect and allow us to understand, and then improve operations that are too complex for the human mind to manage, in some ways making the previously invisible visible. It will make processes far more agile, efficient and productive. The machine based process improvement is a major disruptor of intelligence management business processes. That offers new markets that are looking to find major improvement to managing vast amount a data that requires a new approach in its consumption and providing better and faster analysis in new world of Big Data.
Terrain Dominance Analytics Platform for Intelligence (TDAPI) comes into play when requirements include intelligence over time as preventative measure by identifying terror hubs,integrate targeted intelligence information and actionable intelligence ahead of special operations or strategic deployment of troops and for law enforcement that support “safe city” programs.
TDAIP is based on multi-dimensional technological intelligence gathering capabilities by integrating scraped Social Sites and Net-messaging, Cell phone calls, Behavior Patterns, Video, Sensor systems (optic, radar, acoustic, electromagnetic installed on board various platforms, underground, on the surface, at sea, in the air and in space – comprehensive, continuous intelligence is generated by combining and integrating these qualifiers could provide analytics that offers Terrain Dominance capabilities to military and law enforcement forces.
Integrating, fusing and comprehending the data leads to operational insights. This capability relies on advanced data management foundation which is at the heart of TDAIP since it unites different sources of data, identifies patterns and alterations across the area of interest – changes on the ground or in population behavior or others deltas in the data flow.
For military activity , the GIS-based Command and Control system displays the threats, enables threat-analysis over time, prioritization of threat levels and the considered activation of response capabilities. The C4I system enables managing the intelligence, operational and logistic efforts – including data dissemination, supporting command hierarchies and providing investigative tools for later analysis and drawing lessons learned.
At an age of terror, asymmetrical warfare, as the main threat – along with response capabilities based on unmanned autonomous vehicles, special units and preventative capabilities – TDAPI is a necessity for every modern, advanced military and law enforcement. To achieve just in time Terrain Domain Intelligence advantage automated methodology needs to be used by law enforcement operations to combat terrorism that threatens non-military targets in large cities or on other high profile civilian activities like city festivities This type of dominance and control requires seeing patterns everywhere and combine “big data” and data analytics to show patterns in multiple walks of life.
By connecting big data architecture that integrates operational systems of all types with social media for example leveraging user centric or data scientist focused technology design, the software could track and identify potential target activity behavior patters that continuously experience dynamic alterations.
This software uses mathematical models to read social media and analyze key identifiers or classifiers. It also could taps into satellite, street cameras or UAV imagery in order to create an image that reads the different moods or emotional states of pockets of the population in a integrated manner. That technology sounds like sci-fi but technologies for that type of analysis is available for early adopters.
As an example it offers a visual representation, where analyst could generate an image of mid-town New York that shows the part of the city covered with a multitude visual identifiers of people that get translated from face recognition, walking patterns etc to identify a target profile that is defined by profilers that stored in the platform libraries. For example based on qualifiers the patterns of anger or other criteria could be marked as red. By using deep learning technology the software becomes more accurate exponentially.
In addition, TDAPI should build up incrementally libraries of algorithms aim to re-design the process cycle just like humans did during the original reengineering movement. Then, reengineering was limited by the speed of humans. Managers noted historical trends and revised processes, and engineers developed code that was then baked into computing systems. Every update or response to the process change required multiple steps; it cost time and performance. Sometimes, by the time changes were in place, the demographics of the target had already moved or changed. With machine based reengineering approach, process changes are constant and driven not just by history but also by the predictive capabilities of machine-learning algorithms. Machine-learning asks that people train and actively manage the performance of the algorithms and data models that drive process change,
By adding self-service real time data management with embedded analytics will change people’s expectations for good. According to Gartner, in 2016-2017, people will seek empowerment across the information continuum, especially as more millennials enter the workforce. For business,military and law enforcement users to stay effective, they must be able to shape certain data on the fly. That’s why the demand for self-service data preparation tools service data analysis will grow. This democratization of data,information and even knowledge will allow people to respond quickly to changes in data patterns and will require near real time adjustments in data streaming and analysis modeling and ultimate products such as prescriptive or predictive analytics. As part of the same trend data preparation will be part of “Data as a Service” architecture There is also benefits in leveraging machine learning techniques to surface patterns and correlations in the data, thus integrating “intelligence” to the data preparation process and strengthening security and reusability as part of cognitive self service or embedded data architecture.
Census data and mapping have for centuries provided invaluable information on the make-up of a city, however the up-to-now unavoidable delays in data gathering, analysis, and application have presented challenges to timely response to evolving threats. Sampling has been the basis of traditional methods of data collection and analysis, but while it has been useful, it is not lacking in shortcomings. With sampling rates of n=’some hundreds’ the extrapolated informations lacks depth and accuracy. Big Data allows analysts to tackle issues with sampling rates of n=’all,’ allowing for a deeper, more accurate, and granular approach to understanding populations.
What’s more, up-to-date data obtained from a multitude of source (credit card transactions, mobile phone data, video etc.) assure that the picture derived from it is far more accurate and true to reality than that from self-reported data. Most of this doesn’t require additional investment, as the data is a “byproduct” of normal operations for cities and companies. The treasure trove of information is left unused, and utilizing it should require little additional cost, while the benefits are great.
It is important to create effective and efficient data driven behavior platform to identify and prioritize integration internally or externally with existing or future technologies brands that focus on accurate real time mapping and imaging application and emotional analytics that allow you to focus on one’s core competency at the the time and allow faster time to market.. When it comes to predictive analytics for some of the applications there is a need of longitudinal data or the data that is aggregated with a certain frequency that will require dynamic changes in the model. The real “ game changer “ for TDAIP ecosystem will be the Internet of Things (IoT) which is the network of physical objects which enables these objects to collect and exchange data using unique IP addresses. The Internet of Things allows objects to be identified and enabled remotely across the network infrastructure offer opportunity for more direct integration between the physical devices and traditional IT hardware and software Each physical object is uniquely identifiable through the embedded computing system but is able to interoperate within the existing network infrastructure.
To sum up the technical solution should be able to unify general intelligence operational data sources with the field based TTDIP data sources described above to be processed in batch, real-time or near real time by the TDAIP platform to provide SME’s with predictive or prescriptive analysis using graphical or GIS based interfaces.
How does TDAIP could facilitate prevention of terrorist acts similar to the one we saw in Paris and Brussels?
The example is generic and takes into account availability of Data Inputs that are available in a municipal terrain. First, the TDAIP integration and Analytical Platform needs to input for monitoring purposes should include but not limited the following sources
The input systems
- Physical Security Information Management (PSIM)-often part of “safe city” IT programs or sensitive locations protection systems.
- Law Enforcement and Intelligence Operational systems
- Sensor Network ICT Systems – IoT
- Wireless Sensor Networks – sensors that using wireless networks to communicate identification parameters
- Social media data interfacing – most common method in identifying radical communication
- Cell information technology monitoring – monitoring cell phone communication
- Intelligent Video Surveillance – video monitoring with face or other parameters identifiers.
Safe City Communication and Infrastructure
- Crowd Surveillance – video monitoring of crowd using video, cell or sensor technology
- Physical Identity and Access Management (PIAM) Biometric or other type of scanning methods to control access to sensitive locations or terrain
- Suspect location based services – identifying location of cell phone or other digital devices using advanced GPS capabilities
Potential processing enablers
The following includes but not limited to processing enablers:
Sensor and Data Fusion Algorithms, Intelligent Video Surveillance (IVS) Technologies, Cloud Platforms, Behavioral Analyses, Real Time Automatic Alerts Software, Image Segmentation Software, Item Tracking Intelligent CCTV Surveillance Software, Object Sorting and ID, Item Identification and Recognition,, License Plate Recognition (LPR), Sorting Actions and Behaviors, Video Content Analysis, AI based Behavioral Profiling, Tag and Track, Kalman Filtering Techniques, Region Segmentation), Partially Observable Markov Decision Process, ‘Splitting’ items Algorithms, Dimension Based Items Classifiers, Shape Based Item Classifiers, Event Detection Methods, Vision-based Human Action Recognition, 3D Derived Egomotion, Path Reconstruction Software.
The amount of available data is growing and there is no sign of a slowdown. To better protecting the peace and safety of the population, companies that provide TDAIP products and services will assist military, intelligence and law enforcement services to harness it, analyze it with achieving strategic and tactical advantage in cities or even on military fields.